TYPES OF CYBER ATTACKS
DOS Attack :
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the theft or loss of significant information or other assets, they can cost the victim a great deal of time and money to handle.
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing them to slow down and eventually stop. Popular flood attacks include:
- Buffer overflow attacks – the most common DoS attack. The concept is to send more traffic to a network address than the programmers have built the system to handle. It includes the attacks listed below, in addition to others that are designed to exploit bugs specific to certain applications or networks
- ICMP flood – leverages misconfigured network devices by sending spoofed packets that ping every computer on the targeted network, instead of just one specific machine. The network is then triggered to amplify the traffic. This attack is also known as the smurf attack or ping of death.
- SYN flood – sends a request to connect to a server, but never completes the handshake. Continues until all open ports are saturated with requests and none are available for legitimate users to connect to.
Other DoS attacks simply exploit vulnerabilities that cause the target system or service to crash. In these attacks, input is sent that takes advantage of bugs in the target that subsequently crash or severely destabilize the system, so that it can’t be accessed or used.
The primary focus of a DoS attack is to oversaturate the capacity of a targeted machine, resulting in denial-of-service to additional requests. The multiple attack vectors of DoS attacks can be grouped by their similarities.
How DOS Attack Works :
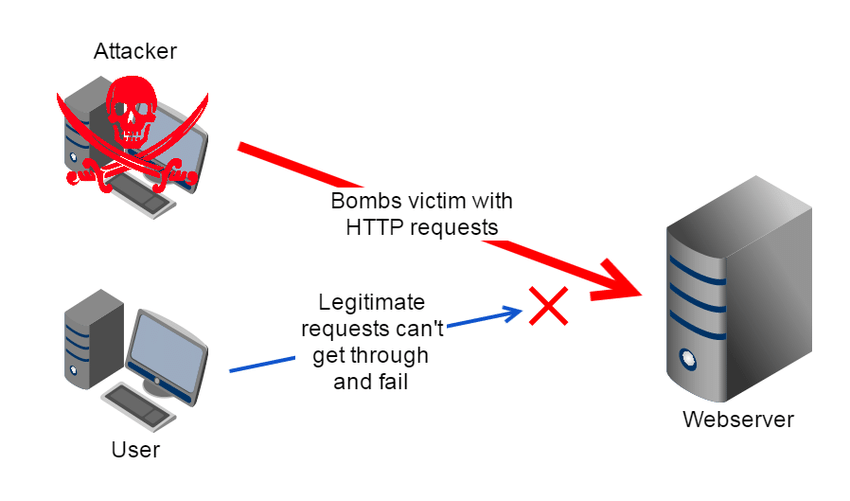
DDoS (distributed denial-of-service ) Attack :
A distributed denial-of-service (DDoS) attack is a type of DoS attack that comes from many distributed sources, such as a botnet DDoS attack.

DoS Vs DDoS :
| DoS | DDoS |
|---|---|
| DOS Stands for Denial of service attack. | DDOS Stands for Distributed Denial of service attack. |
| In Dos attack single system targets the victims system. | In DDos multiple system attacks the victims system. |
| Victim PC is loaded from the packet of data sent from a single location. | Victim PC is loaded from the packet of data sent from Multiple location. |
| Dos attack is slower as compared to ddos. | DDos attack is faster than Dos Attack. |
| Can be blocked easily as only one system is used. | It is difficult to block this attack as multiple devices are sending packets and attacking from multiple locations. |
| In DOS Attack only single device is used with DOS Attack tools. | In DDos attack Bots are used to attack at the same time. |
| DOS Attcaks are Easy to trace. | DDOS Attacks are Difficult to trace. |
| Volume of traffic in Dos attack is less as compared to DDos. | DDoS attacks allow the attacker to send massive volumes of traffic to the victim network. |
How to avoid DOS Attack :
- Buy More Bandwidth
- Build Redundancy Into Your Infrastructure
- Configure Your Network Hardware Against DDoS Attacks
- Configure Your Network Hardware Against DDoS Attacks
- Deploy A DDoS Protection Appliance
- Protect Your DNS Servers
TYPES OF CYBER ATTACKS
- Man In The Middle Attack
- Brute Force & Dictionary Attack
- SQL Injection
- Botnet
- Trojan Horse
- Malware Attack
- Cryptojacking
- Phishing
- Session Hijacking
- DNS Spoofing
- DOS Attack
Did you like our works?
We are known for Website Development and Website Designing, along with Android iOS application development in Mumbai, India.
