TYPES OF CYBER ATTACKS
BOTNET :
BOTNET = BOT(Robot) + NET(Network)
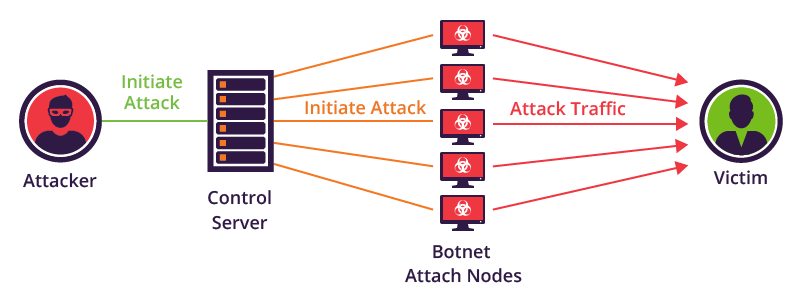
A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection.
A botnet is a network of infected computers which, under the command of a single master computer, work together to accomplish a goal.
A botnet relies on two things: for one, it needs a large network of infected devices, known as “zombies”, to do the grunt work and heavy lifting for whatever scheme the hacker has planned. Secondly, you need someone to actually command them to do something blindly, frequently called the Command and Control center, or “bot herder”.
How to avoid Botnet Attack :
- Good security begins with an Internet security suite that detects malware that has been installed, removes what’s present on your machine and prevents future attacks.
- Always update your computer’s operating system as early as possible. Hackers often utilize known flaws in operating system security to install botnets. You can even set your computer to install updates automatically.
- The same is true of applications on your computer, phone and tablet. Once weaknesses are found and announced by software companies, hackers rush to create programs to exploit those weaknesses.
- Don’t download attachments or click on links from email addresses you don’t recognize. This is one of the most common vectors for all forms of malware.
- Use a firewall when browsing the Internet. This is easy to do with Mac computers, as they come with Firewall software pre-installed. If you’re using a Windows-based machine, you might need to install third-party software.
- Don’t visit websites that are known distributors of malware. One of the things that a full-service Internet security suite can do is warn you when you’re visiting such sites. When in doubt, check with Norton Safe Web.
TYPES OF CYBER ATTACKS
- Man In The Middle Attack
- Brute Force & Dictionary Attack
- SQL Injection
- Botnet
- Trojan Horse
- Malware Attack
- Cryptojacking
- Phishing
- Session Hijacking
- DNS Spoofing
- DOS Attack
Did you like our works?
We are known for Website Development and Website Designing, along with Android iOS application development in Mumbai, India.