TYPES OF CYBER ATTACKS
Man in the Middle (MITM) :
Man-in-the-Middle attack is the type of a cybersecurity breach that allows an attacker to snoop a communication between two individuals. The attack occurs between two legitimate communicating entities, enabling attacker to intercept communication they should otherwise not be able to access. Thus the name “man-in-the-middle.” The attacker “eavesdrop” to the conversation by obstruct the public key message transmission and retransmits the message while interchanging the requested key with his own. The two parties appears to communicate as usual, without knowing that the message sender is an unknown evildoer who is trying to modify and access the message before it is transmitted to the receiver. Thus, the intruder is controlling the whole communication.
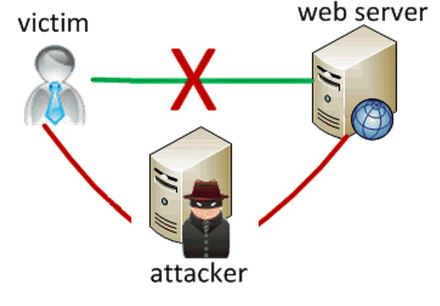
How to avoid Man-In-The-Middle Attack :
- Share and access the private information over encrypted networks only (Eg. WAP, WPA, WPA2 networks).
- Avoid using your personal login credentials in the public locations(Eg. cafes and airports etc.) where the internet is not secured and unencrypted.
- When accessing confidential business accounts like bank accounts, ensure that you are connected to an HTTPS website and not on HTTP websites as HTTPS is more secured than HTTP.
- To add more security, you can also use VPN services which you can turn on when you are accessing sensitive information over the unsecured network.
- Make sure that the DNS servers (DNS caches) that we use are secure or not. Check the configuration on your router (DNS cache addresses are usually provided by the DHCP). Use Google public DNS caches: 8.8.8.8 and 8.8.4.4.
TYPES OF CYBER ATTACKS
- Man In The Middle Attack
- Brute Force & Dictionary Attack
- SQL Injection
- Botnet
- Trojan Horse
- Malware Attack
- Cryptojacking
- Phishing
- Session Hijacking
- DNS Spoofing
- DOS Attack
Did you like our works?
We are known for Website Development and Website Designing, along with Android iOS application development in Mumbai, India.
